 bizhub
bizhub

According to Verisign's latest report, 25 per cent of attacks in Q2 2017 peaked to over five Gigabits per second (Gbps).
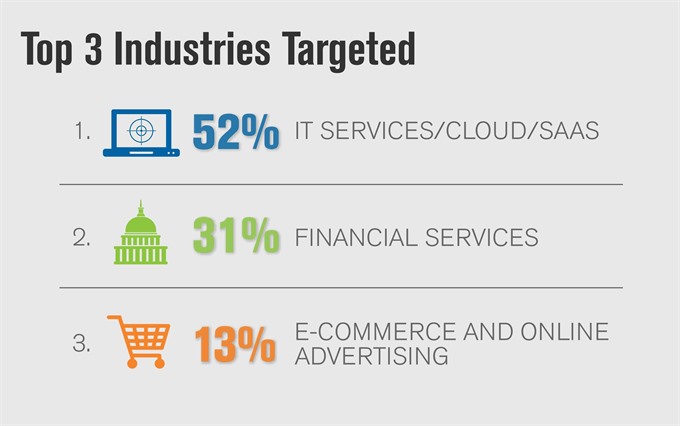 |
| The IT/Cloud/SaaS industry, representing 52 per cent of mitigation activity, was the most frequently targeted industry for the eleventh consecutive quarter. — Photo Verisign |
HÀ NỘI — According to Verisign’s latest report, 25 per cent of attacks in Q2 2017 peaked to over five Gigabits per second (Gbps).
However, the average peak attack size decreased 81 per cent compared with the previous quarter.
The Q2 2017 DDoS Trends report said the number of attacks had decreased since Q1 2017. Overall, average peak attack sizes have decreased since Q2 2016.
“Seventy-four per cent of the DDoS attacks mitigated by Verisign in Q2 2017 employed multiple attack types. Fifty-seven per cent of DDoS attacks were UDP Floods. TCP-based attacks were the second-most common attack vector, making up 20 per cent of attack types in the quarter,” the report stated.
The IT/Cloud/SaaS industry, representing 52 per cent of mitigation activity, was the most frequently targeted industry for the eleventh consecutive quarter. The financial sector industry experienced the second-highest number of DDoS attacks, representing 31 per cent of mitigation activity. The largest volumetric and highest intensity DDoS attack observed by Verisign in Q2 2017 was a multi-vector attack that peaked to approximately 12 Gbps and some one million packets per second (Mpps). This attack sent a flood of traffic to the targeted network for about an hour, abated for an hour, and then set another wave of traffic for an additional hour, according to the report.
There are two main types of cyber-attacks that companies face today which involve ransom and extortion -- Ransom attack and DDoS extortion attack. Two recent global ransomware attacks, WannaCry and NotPetya, have increased public visibility of the devastating effects that ransomware can have on an organisation’s critical assets.
The WannaCry ransomware attack affected more than 300,000 computers in more than 150 countries. The NotPetya ransomware attack was more destructive. It spread faster than the WannaCry ransomware and caused “permanent and irreversible damage” to a computer’s hard drive. One report shows that in 2016, almost half of United States-based companies faced a ransomware incident.
The report said Domain Name System (DNS) controls can play an important role in helping to identify and protect users from malware and ransomware attacks. When DNS resolvers utilise security risk information feeds, such information can be leveraged to set up filters to proactively analyse and identify Command and Control connection mechanisms. Such filters can help to stop the encryption process leveraged by many ransomware strains. — VNS
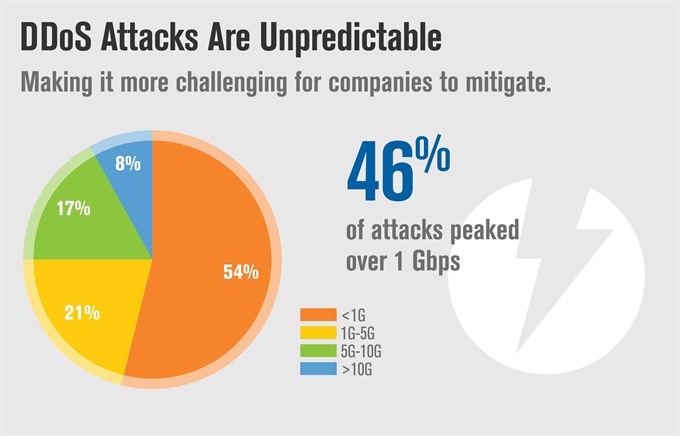 |
| According to Verisign’s latest report, 25 per cent of attacks in Q2 2017 peaked to over five Gigabits per second (Gbps). — Photo Verisign |




