 advertisement
advertisement

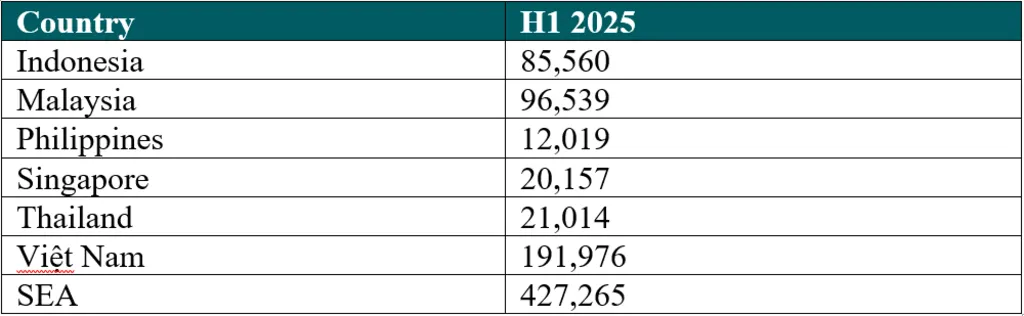 |
Việt Nam recorded 191,976 incidents in the first half of 2025, up significantly from 107,363 cases during the same period in 2024. This equates to approximately 1,055 spyware attacks per day over the six-month period. With this 78.8 per cent increase in attack dynamics, Việt Nam remains one of the top three countries in Southeast Asia for the most spyware activities, following Singapore (+210.9 per cent) and Malaysia (+124.2 per cent).
The global cybersecurity company notes that the stark rise in targeted spyware attacks rippling through corporate Việt Nam is a wake-up call to firms across the country.
Spyware is a type of software secretly installed on a user’s computer or mobile device to collect their data.
Unlike some forms of malware, spyware typically does not harm the operating system, programs, or files. Instead, it runs on the device to monitor activity (e.g., keylogging, screen captures). While it can be installed via online means, its surveillance often happens locally.
 |
Step-by-step, spyware typically takes the following actions on a computer or mobile device:
• Infiltrate: It gains entry via an app install package, a malicious website, or a file attachment.
• Monitor and Capture Data: It records data via keystrokes, screen captures, and other tracking codes.
• Exfiltrate Data: It sends the stolen data to the spyware author, to be used directly or sold to other parties.
• In short, spyware communicates personal, confidential information about the victim to an attacker.
The information gathered may be general, such as online browsing habits or purchases, but the spyware code can be modified to record more specific activities.
Data commonly compromised by spyware includes:
• Login credentials (passwords and usernames)
• Account PINs
• Credit card numbers
• Monitored keyboard strokes (Keylogging)
• Tracked browsing habits
• Harvested email addresses
Recent years have also witnessed the emergence of commercial spyware, a form of "legal malware" often sold to governments and law enforcement, which has become an urgent threat to organisations globally.
Commercial spyware functions like malware developed by private firms, designed to secretly monitor devices by stealing messages, eavesdropping on calls, tracking locations, and removing all traces of its presence. Installation often exploits zero-click vulnerabilities, meaning victims do not even need to click anything for the infection to happen.
Pegasus is among the most infamous commercial spyware. It is known for its ability to zero-click infect devices via iMessage, WhatsApp, and other platforms and is capable of full device surveillance including messages, calls, and location tracking. In 2024, Kaspersky’s Global Research and Analysis Team (GReAT) developed a lightweight technique to spot traces of advanced iOS spyware like Pegasus, Reign, and Predator by examining Shutdown.log, a forensic trail that had gone largely unnoticed.
In Việt Nam, Kaspersky’s report revealed that the number of spyware attacks against businesses here surged to 191,976 in the first half of 2025, from just 107,363 incidents in the same period last year.
“Việt Nam is seeing strong developments in technological applications,” comments Simon Tung, General Manager for ASEAN and Asia Emerging Countries (AEC) at Kaspersky. “However, all digitalisation activities carry the risks of data theft. The platforms are bustling with business deals, social networking, and brand promotions, which has expanded the digital footprint of users, creating more entry points for attackers.”
Tung added, “Valuable information such as login credentials, financial data, phone numbers, or purchase history are what attackers want to capture for fraudulent activities. It is urgent for businesses here to transition to using threat intelligence platforms to proactively detect, assess, and respond to damaging attacks like spyware.”
Ensuring full protection against attacks using spyware is generally challenging. However, organisations can at least make life harder for potential attackers. Kaspersky suggests the following recommendations:
• Regularly update the software on all devices, prioritising operating systems, browsers, and messaging apps.
• Do not click on suspicious links - one visit to a malicious site may be enough to infect your device.
• Use a VPN to mask your internet traffic; this will protect you from being redirected to a malicious site while browsing HTTP pages.
• Reboot regularly. Often, spyware cannot persist in an infected system indefinitely, so rebooting helps get rid of it.
• Install a reliable security solution on all your devices.
• Use the latest Threat Intelligence information to stay aware of the actual Tactics, Techniques, and Procedures (TTPs) used by threat actors./.




