 Economy
Economy

|
HCM CITY — ScarCruft, a Korean-speaking threat actor, has tested and created new tools and techniques, and extended both the range and volume of information collected from victims.
Among other things, the group has created code able to identify connected Bluetooth devices, according to Kaspersky Lab.
The group’s attacks begin, like many other ScarCruft advanced persistent threats (APTs), with either spear-phishing or strategic website compromise, also known as ‘watering-hole’ attacks, using an exploit or other tricks to infect certain visitors.
Kaspersky Lab researchers uncovered an interest in stealing data from mobile devices and malware that fingerprints Bluetooth devices using the Windows Bluetooth API.
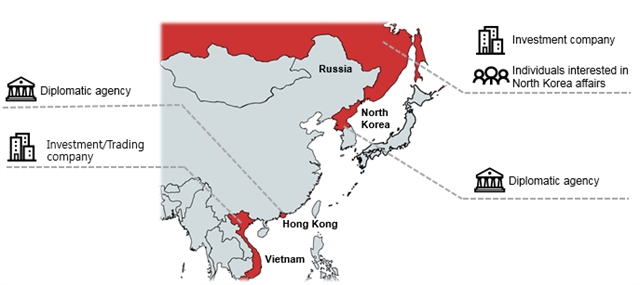
Based on telemetry data, victims of this campaign include investment and trading companies in Việt Nam and Russia that may have links to North Korea, and diplomatic entities in Hong Kong and North Korea.
Seongsu Park, senior security researcher, global research and analysis team at Kaspersky Lab, said: “This is not the first time we have seen ScarCruft and DarkHotel overlap. They have similar interests in terms of targets, but very different tools, techniques and processes. This leads us to believe that one group regularly lurks in the shadow of the other.
“ScarCruft is cautious and likes to keep a low profile, but it has shown itself to be a highly-skilled and active group, with considerable resourcefulness in the way it develops and deploys tools. We strongly believe that it will continue to evolve.”
To avoid falling victim to a targeted attack by a known or unknown threat actor, the company’s researchers recommend users to implement measures such as keeping up to date with new and emerging tools, techniques and tactics used by threat actors and cybercriminals, implementing endpoint detection and response, and having a corporate-grade security solution that detects advanced threats on the network level at an early stage. — VNS



.jpg)





